Zero-day attacks discovered in-the-wild, Arkei Stealer and LimeRAT boosting their presence, and continuation of pro-russian DDoS attacks
Foreword
Welcome to the latest edition of the Avast Threat Report, which covers Q4/2022. As we’ve closed 2022 and have entered 2023, we look back at the challenges of the final quarter of last year and the many new threats and malware strains that emerged during it. 2022 was a challenging year for cybersecurity, and its last quarter was no exception. The threat landscape continued to evolve at a rapid pace, and individuals as well as organizations of all sizes were faced with new and increasingly sophisticated attacks. In this report, we will take a closer look at the trends and developments that took place during Q4, providing valuable insights into the current state of cybercrime.
From my point of view, one of the most interesting things from Q4/2022 wasn’t directly related to malware (at least for now). I’m referring to the launch of ChatGPT, a chatbot developed by OpenAI. Some people have already started using it as a virtual assistant for creating short code sequences, explanation of assembly code, or even writing a paragraph in a report foreword (wink-wink). No matter the tool’s inaccuracy or how many generic phrases or false things it produces, ChatGPT is already being analyzed by cybercriminals with malicious intentions. The creation of phishing messages as well as generating simple code snippets for script-kiddies is low-hanging fruit, but it’s too early to say how the malicious uses of ChatGPT will continue in the upcoming year.
Within more traditional threat topics, this report will focus on awesome discoveries of my colleagues who discovered, blocked, and responsibly disclosed two zero-days used in the wild by advanced threat actors (CVE-2022-3723 and CVE-2023-21674). Of a similar importance was a great hunt for Mustang Panda in Myanmar that we reported on in depth.
Furthermore, we will focus on a flood of DealPly adware that took place in Brazil and Europe. Similarly, there was a quadruple growth of the Arkei Stealer prevalence worldwide and triple for LimeRAT, especially in Asia and Latin America. Next, as Bitcoin was hitting its local lows in Q4/2022, the situation was dramatically different with malicious coinmining activity, where the Balkan states were especially heavily targeted. Moreover, technical support scams (TSS) peaked in this quarter.
Threat actors also demonstrated their creativity when dealing with deprecation of their favorite infection vector: Office documents. We already touched this topic in the Q3 Report, but the malware authors continued with their effort and employed techniques such as HTML smuggling, SEO poisoning, and the injection of Office templates in their latest malware campaigns.
The situation on mobile was also thrilling with the new Bully Facestealer or the BrasDex banker that automates fraudulent payments. At the same time, adware won (by a landslide) its number one position as the most prevalent mobile threat.
Unfortunately, ransomware still has not been eradicated. However, the fight against it continues with particular successes; for example, one of the Netwalker ransomware affiliates will enjoy well-deserved jail time and we also decrypted the MafiaWare666 ransomware and provided a free decryption tool for its victims.
And finally, I can also recommend the story about DDosia, an attack tool developed and used by a pro-russian group, which also resulted in trying to interfere with the Czech presidential election in early January 2023. We hope you enjoy reading the following deep dives into each of the aforementioned threats and findings.
Jakub Křoustek, Malware Research Director
Methodology
This report is structured into two main sections: Desktop-related threats, where we describe our intelligence around attacks targeting the Windows, Linux, and Mac operating systems, including a special focus on web-related threats, and mobile-related threats, where we describe the attacks focusing on the Android and iOS operating systems.
Furthermore, we use the term risk ratio in this report to describe the severity of particular threats, calculated as a monthly average of “Number of attacked users / Number of active users in a given country.” Unless stated otherwise, calculated risks are only available for countries with more than 10,000 active users per month.
Desktop-Related Threats
Advanced Persistent Threats (APTs)
One of the most active APT campaigns was ShadowPad/ScatterBee, which spread in Pakistan during Q4/2022. Nevertheless, there was another APT campaign discovered by our team that was even more significant and impactful: A strong activity from Mustang Panda targeting Burmese government institutions and Burmese human rights activists. We gained new insights into their activities and campaigns, but their operations retain a similar modus operandi and targets. We recently presented our research on “Hitching a ride with Mustang Panda” at the AVAR conference.
Mustang Panda
We published a report on an espionage operation in Myanmar that we attributed to Mustang Panda. We also presented our findings on this operation at the AVAR conference for security researchers. According to our telemetry, we found that some of Myanmar government institutions were relentlessly attacked and breached. Mustang Panda was exfiltrating sensitive documents, recordings, and email dumps including scans of passports from Asian, American, and European citizens and diplomats applying for Burmese visas, from Burmese human rights activists Burmese government institutions.
The operation was identified when we discovered a distribution server linked to a malware infection in Myanmar. While the primary exfiltration path went through Google Drive, the files from Google Drive were later on moved to the distribution server. Once the threat actor retrieved the data from the distribution server, the data was deleted. This means that we could nevertheless access only a limited part of the data. Since the throughput was usually gigabytes of data per day, we have managed to establish a basic victimology to be able to inform affected parties.
While the used tooling contained Mustang Panda’s staples such as Korplug or Delphi USB installer, most of the discovered tools were rather simplistic and without sophisticated obfuscation. DLL side-loading has been a common theme for most of the tools found during the analysis.
Luigino Camastra, Malware Researcher
Igor Morgenstern, Malware Researcher
Adware
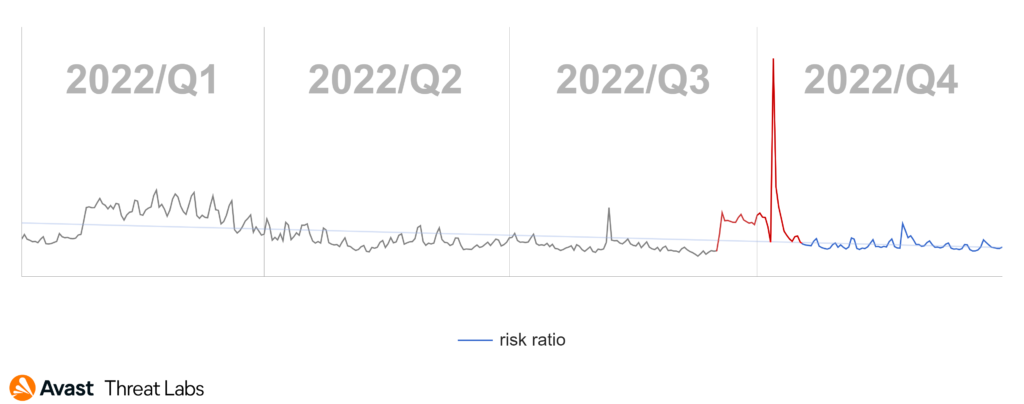
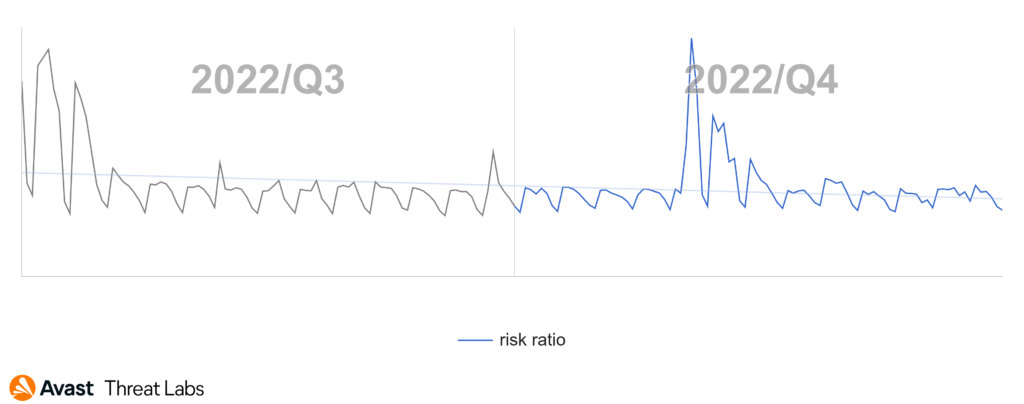
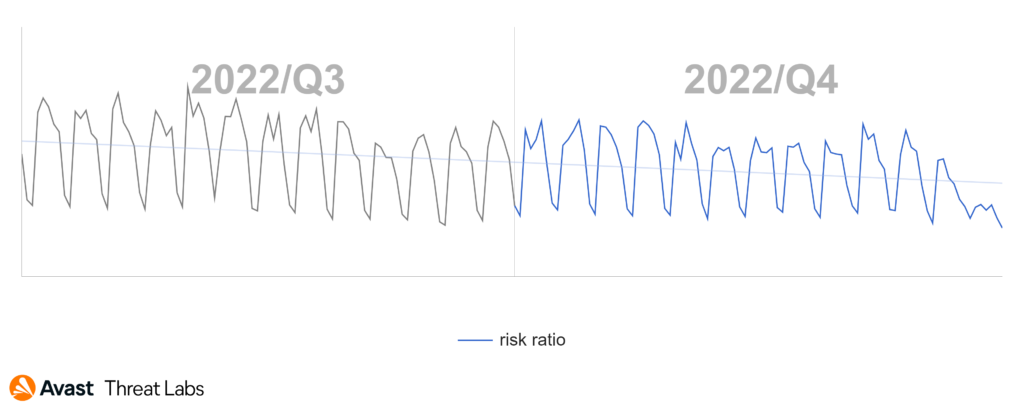
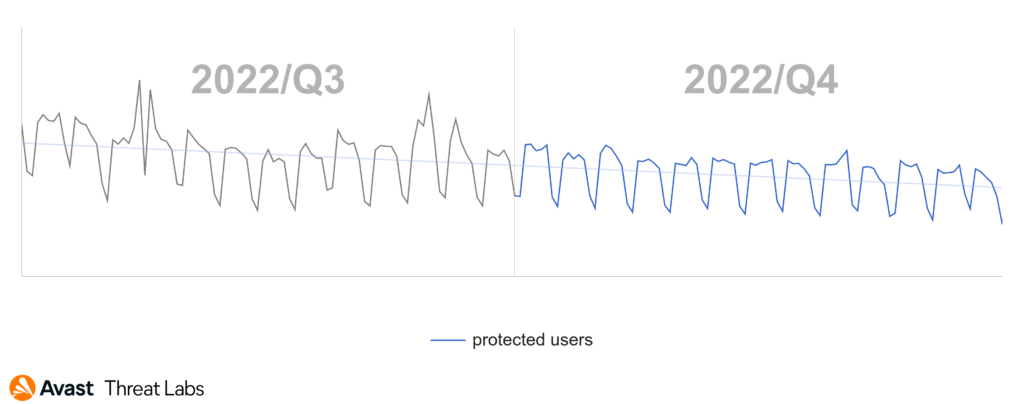
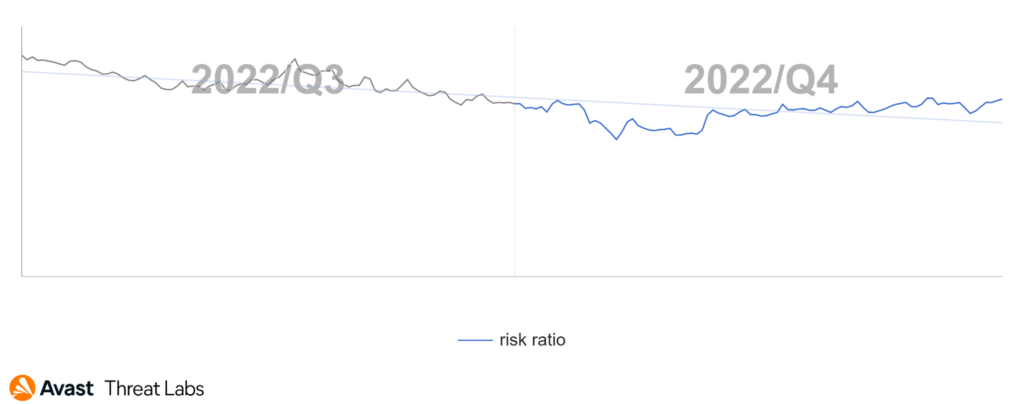
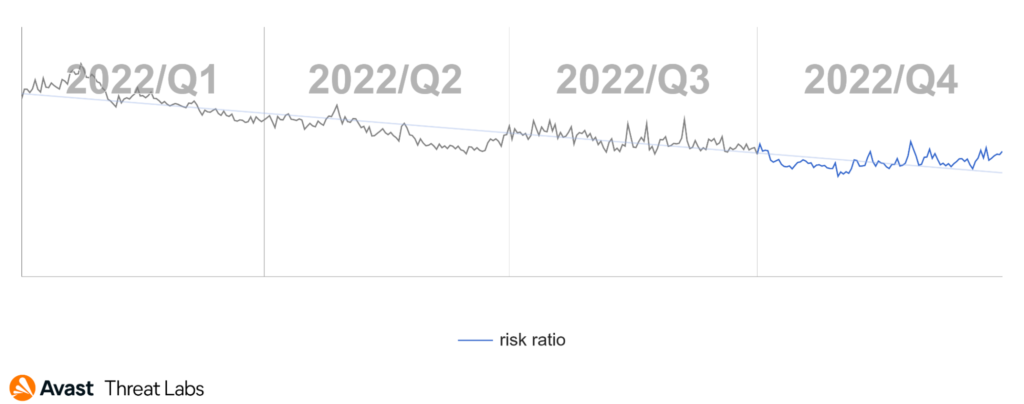
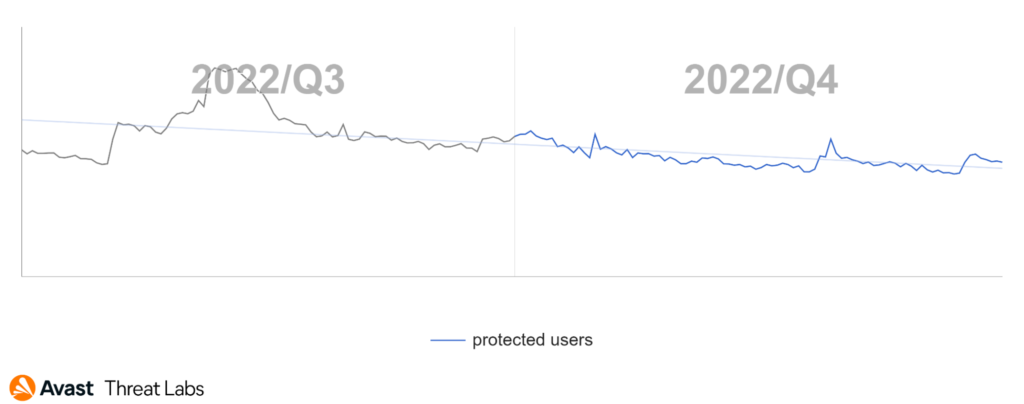
At the end of Q3/2022, we recorded the rapid rise of the adware activities that were continuing into the beginning of Q4/2022, as the graph below illustrates.
The rise at the turn of the quarters is an effect of the DealPly adware that we introduced in the previous Q3/2022 Threat Report. The DealPly family is classified as an unwanted application because it can be installed silently with some other browser extensions and free software but also via malware.
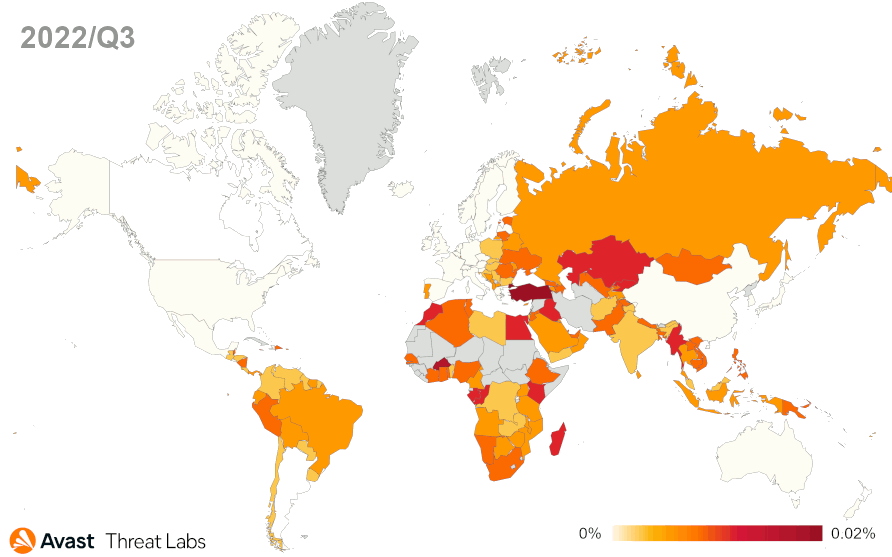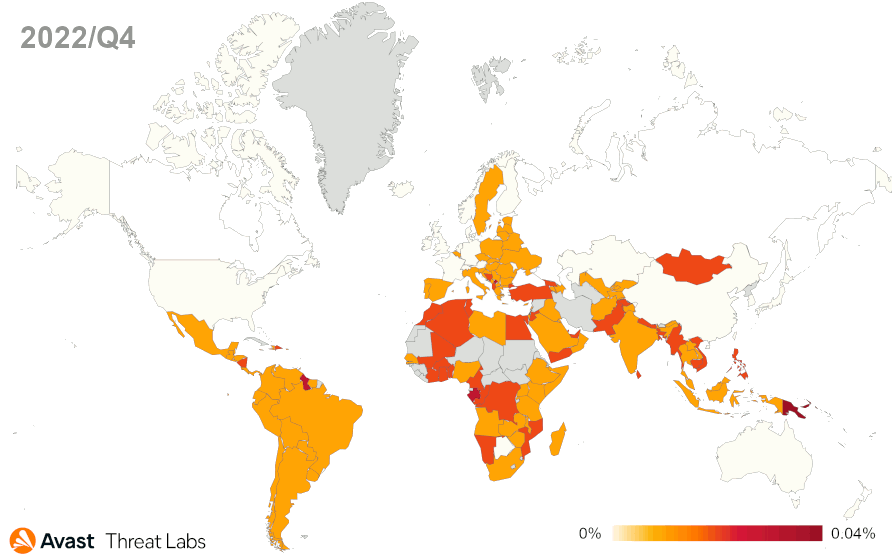
In Q4/2022, DealPly’s risk ratio was higher in most countries compared to the previous quarter. The risk ratio for DealPly adware remained the same or slightly increased in Asia, but there are some outliers. The DealPly risk ratio increased in South and Southeast Asia; namely India, Myanmar, and Indonesia. A more significant increase in DealPly’s risk ratio was also observed in many European countries. As animated in the map below, we registered a most significant increase in South and North America, especially in Brazil.
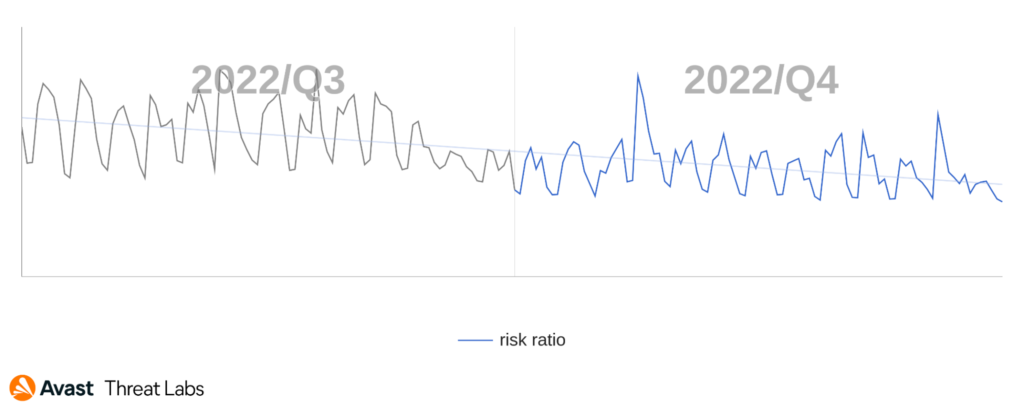
The risk ratio for all adware strains is slightly higher than in Q3/2022, although the map below visually demonstrates a considerable spread of adware. The extreme peak of the DealPly adware activity explains this phenomenon. However, there’s a downward year-round trend of adware activity.
Adware Market Share
The clearly identified market leader in adware remains DealPly, which has a 30% share. We assign orders of lower magnitude shares to other strains as follows:
BrowserAssistant(5%)RelevantKnowledge(4%)DownloadAssistant(3%)ICLoader(2%)
However, other unknown strains covered up 30% of the market share in Q4/2022. The strains have a common behavior that waits for a user to click on an arbitrary hyperlink and replaces the original link with one redirecting the user to advertising websites.
The list of the most-seen ad servers and their percentage representation in the wild is as follows:
naigristoa[.]com(48%)ptuvauthauxa[.]com(35%)oovaufty[.]com(8%)go[.]ad2upapp[.]com(4%)saumeechoa[.]com(2%)
Mostly, adware leads on websites to download free software or offer other products. It’s a business model of online spammers that isn’t particularly dangerous from a security point of view; however, it’s terribly annoying for users. What’s more, the theft of personal data, including payment cards, can be hazardous because some ads convince victims that they have won and require contact and payment information. Furthermore, there is still a not negligible group of adware loading inappropriate content with harmful scripts. Adware can then take control of the system and deploy malware, e.g., ransomware, spyware, RATs, etc. Therefore, the presence of adware is a reason to increase attention and secure one’s system with an antivirus program.
Martin Chlumecký, Malware Researcher
Bots
The story of the DDosia project still continues. DDosia is the project of the Russian NoName057(16) hacker group that recruits volunteers to carry out DDoS attacks. This project marked a change in the direction of the said group, as it eventually replaced the Bobik botnet with a project relying on volunteers. At the beginning of December, DDosia’s C&C server was taken down; nevertheless, the group still shares information about their attacks and promotes their project. For this reason, we presume that a new C&C server was set up. Since we started tracking the project on August 1, 2022, we have seen more than 2,200 DDoS targets (390 of which the group referred to as successful), yielding a 17% success rate with approximately 1,000 participants.
If we account for the related, partially coexistent Bobik botnet, we arrive at around 1,400 targets and 190 successful botnets, slashing the success rate to 13%. DDosia also targeted sites associated with the Czech presidential elections, which took place on January 13-14, 2023. Websites of presidential candidates and others presenting the election results were found among the targets being distributed within the DDosia project. Fortunately, given the way the election results are calculated and distributed, even long-term unavailability of the sites wouldn’t affect the election results, and media would be notified through special channels.
We’ve seen some new tricks in the world of malicious documents. If we look at Emotet as an example, the malware uses malicious documents to trick users into manually copying the document into a Microsoft Office Template folder and launching it from there. Since the folder is a trusted location, the usual execution protection is disabled; therefore, opening the document from this folder will trigger the execution of the macros contained within it.
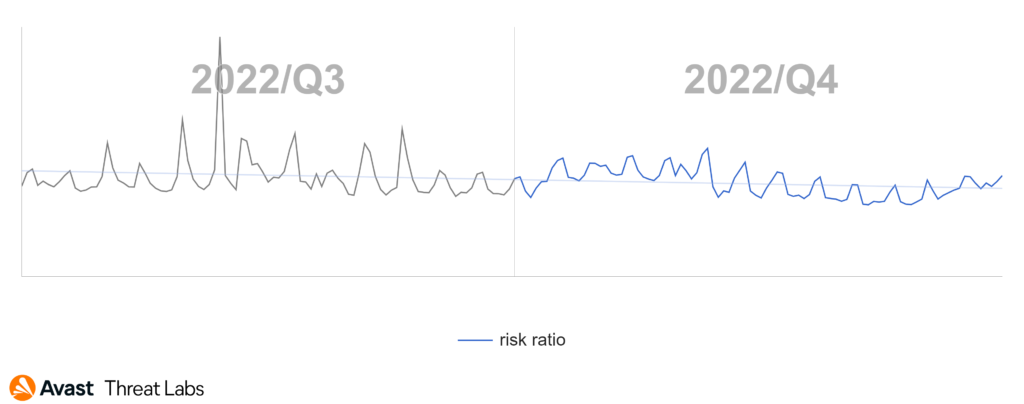
Emotet has also been productive in the evasion technique development. It started to use timers to incrementally proceed in a payload’s execution. We have also observed changes in its communication protocol that are not backward compatible with the previous version of the protocol. As if that wasn’t enough, Emotet has been responsible for the significant peak (see graph below) in the botnet-related risk ratio in early November when it launched a massive spam campaign that mostly utilized variants of Microsoft Excel files (XLS).
Qakbot has also been busy this quarter. The botnet started to use so-called HTML smuggling to hide an encoded malicious script within email attachments. More specifically, they started to abuse SVG images to hide malicious payloads and the code used for their reassembly. Once the user opens the attachment in the browser, the browser launches the code hidden inside the SVG image which, in turn, reconstructs the payload hidden inside the SVG image. The user is then prompted to save a file by the browser and instructed by the “cover” data to open the file. Since the malicious payload is reconstructed on the device, this technique presumably aims to bypass security solutions relying on network traffic analysis.
As for general trends, we’ve seen a significant increase in Qakbot and Amadey’s activity, which has more than doubled. In spite of its massive spam campaign, Emotet has gone through a slight decline. Interestingly, an older .NET open-source botnet, BlackNET, has also seen a significant rise in its activity, which has doubled in comparison to the previous quarter.
Adolf Středa, Malware Researcher
Coinminers
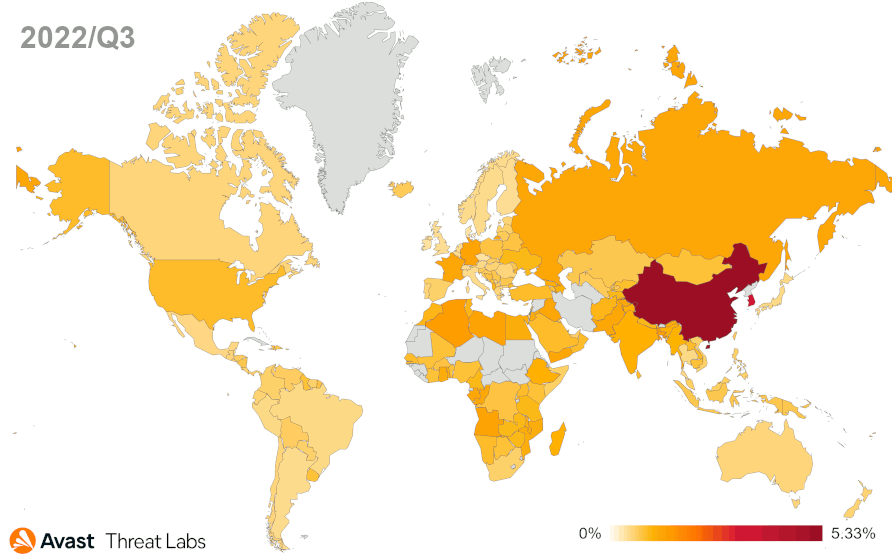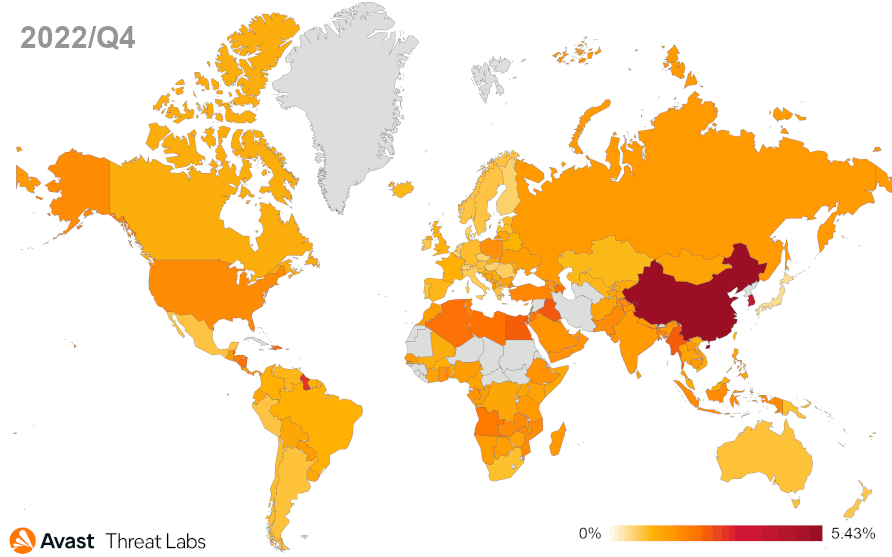
Cryptocurrencies experience difficult times. After turbulent events, such as the bankruptcy of FTX in November 2022, the prices are marking similar low values as at the end of 2020. The same goes for the coinminer activity, as we’ve observed a slight overall decrease (-4%) once again during Q4/2022.
Following the last quarter, users in Serbia were once again most at risk of encountering a coinminer in Q4/2022, with a massive 7.44% risk ratio. The risk ratio of users in Montenegro was 5.99%, followed by Bosnia and Herzegovina with a 3.96% risk ratio, and Madagascar with 3.90%. In Q4/2022, Avast saw a high increase of coinminer activity in Indonesia, resulting in a 46% increase in protected users.
Traditionally, web miners are still on the top of the coinmining food chain with 66% market share, followed by XMRig with 18.42% market share, which increased by 18% compared to the previous quarter. KingMfcMiner continues to grow, having increased its market share by 47% in Q4/2022 (this resulted in a 44% increase of protected users).
The most common coinminers in Q4/2022 were:
- Web miners (various strains)
- XMRig
- CoinBitMiner
- VMiner
- SilentCryptoMiner
- CoinHelper
- NeoScrypt
Jan Rubín, Malware Researcher
Information Stealers
Q4/2022 brought a significant increase in Arkei (also known as its fork Vidar) information stealer, where we protected a whopping 437% more of our users against this threat. We also noticed a respective 57% and 37% increase of users protected against AgentTesla and RedLine stealers. Thankfully, the overall activity of infostealers decreased by 6%, following the trend of the previous quarter, which was mostly due to a decrease in FormBook activity.
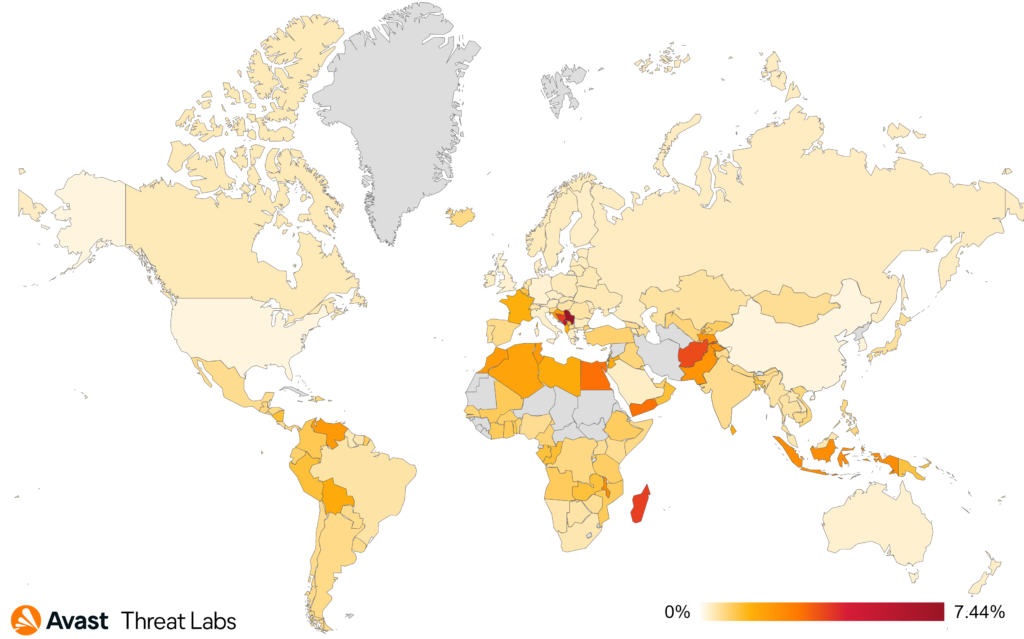
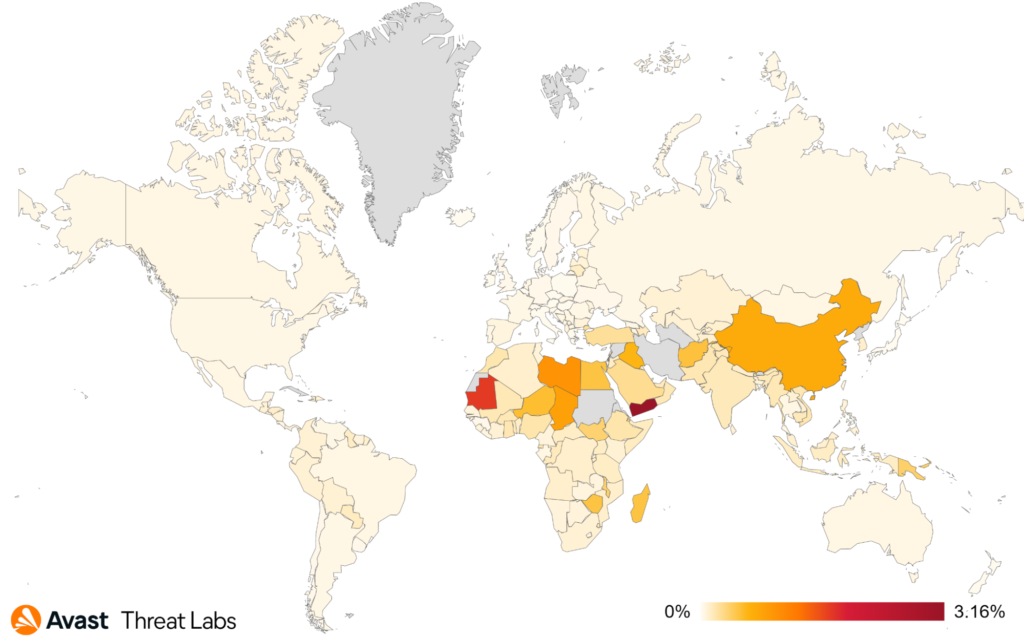
Regarding the risk of being infected by information stealers, the most impacted countries are Yemen, Afghanistan, and Mali. We also protected 21% and 15% more users in Yemen and Afghanistan, respectively. The biggest increases of protected users happened in Mongolia (41%) and Poland (40%).
In Q4/2022, AgentTesla and RedLine were two highly prevalent strains that competed for the second and the third place regarding market share. AgentTesla came in at 15% market share, while RedLine recorded 13%. FormBook still holds the first place with 18% market share, which is a 28% decrease from the previous quarter. After its increase in activity, Arkei now holds 5.21% market share. Despite the ongoing popularity of Raccoon Stealer, which has a 6.26% market share, we noticed a decrease in its activity by 22% during this past quarter.
The most common information stealers in Q4/2022 were:
- FormBook
- AgentTesla
- RedLine
- Lokibot
- Raccoon
- SnakeKeylogger
ViperSoftX spreading VenomSoftX
ViperSoftX is a long-standing information stealer that is undergoing intensive development, providing further malicious functionality in each version.
This multi-stage stealer exhibits interesting hiding capabilities. It’s often concealed as small PowerShell scripts on a single line in the middle of otherwise innocent-looking log files. ViperSoftX focuses on stealing cryptocurrencies, clipboard swapping, and fingerprinting the infected machine as well as downloading and executing arbitrary additional payloads or executing commands.
One of the payloads that ViperSoftX distributes is a specific information stealer that comes in the form of a browser extension for Chromium-based browsers. Due to its standalone capabilities and uniqueness, we decided to give it its own name: VenomSoftX. The malicious extension is highly capable of carrying out a broad range of malicious activity: It provides full access to every page the victim visits, carries out man-in-the-browser attacks to perform cryptocurrency address swapping by tampering with API requests’ data on popular cryptocurrency exchanges, steals credentials and clipboard content, tampers with crypto addresses on visited websites, reports events using MQTT to the C&C server, and more.
As of November 8, 2022, the wallet amounts that ViperSoftX and VenomSoftX redirect stolen cryptocurrencies to summed up to $130,421. This is only the amount sent to cryptocurrency wallets and doesn’t include additional potential profits from other activities.
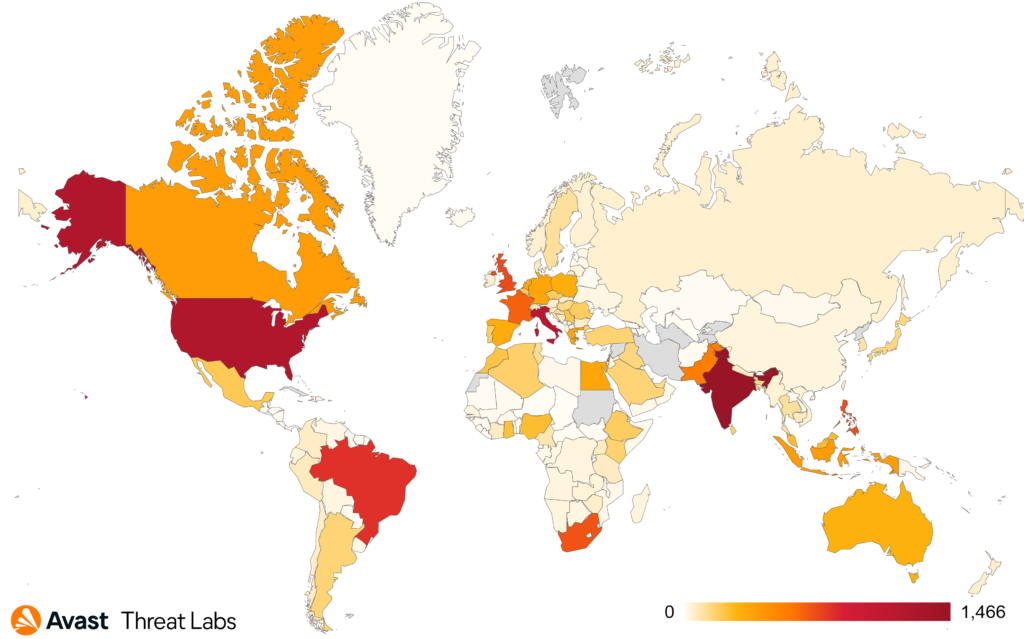
In Q4/2022 alone, Avast protected more than 18,500 unique users from ViperSoftX, where the most impacted countries are India (more than 1,400 protected users), United States (1,200 protected users), and Italy (1,100 protected users).
Raccoon Stealer in the News
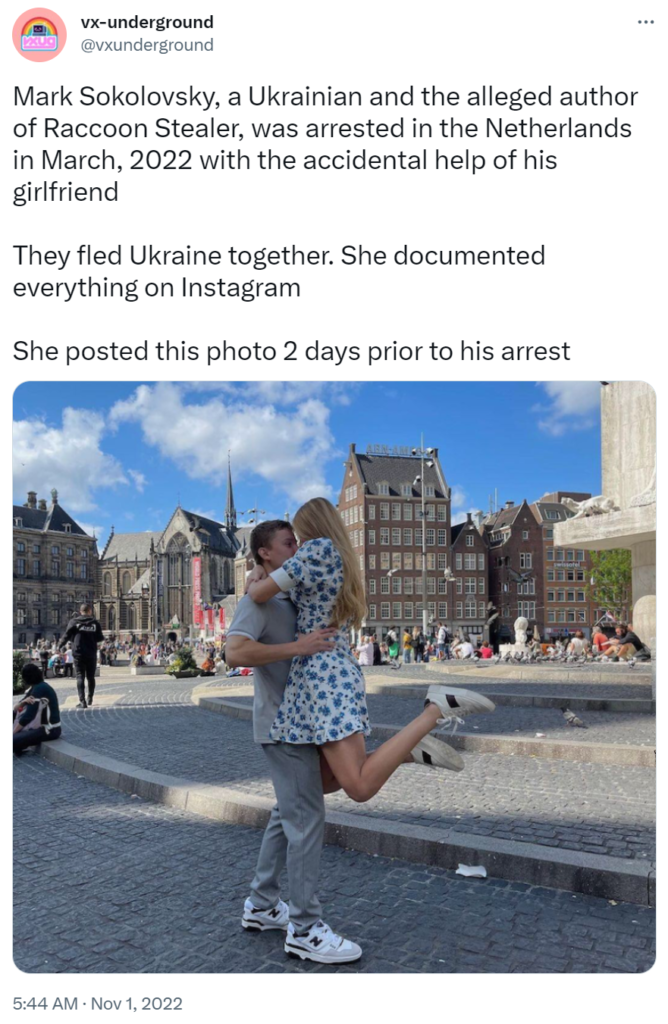
Throughout Q4/2022, we continued to closely monitor Raccoon Stealer, and it isn’t going away anytime soon. One of the news that circulated was the arrest of Mark Sokolovsky, a supposed core developer of Raccoon Stealer, which had happened during March, 2022, in the Netherlands. As we reported previously in Q2/2022, the actors behind Raccoon Stealer announced that their team member died during the war in Ukraine and, thus, they are pausing the development of this infamous malware. However, it is now apparent that the developer was in-fact arrested when he had fled Ukraine.
Funnily enough, as reported by many sources, the key to Sokolovsky’s arrest was actually his girlfriend, who published vacation pictures of the two of them on her Instagram channel.
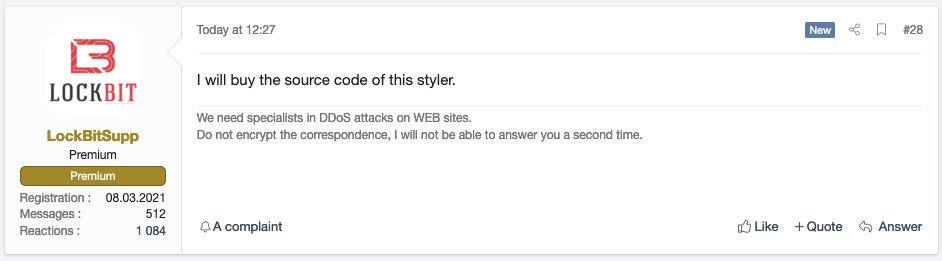
However, as we described in Q2/2022, Raccoon Stealer authors resumed their activity in late June 2022 when they announced Raccoon Stealer 2.0. Their increased activity was reflected in the fact that the group’s popularity has grown in the underground scene as well – around the beginning of November 2022, Lockbit ransomware group expressed interest in buying source code of Raccoon Stealer.
Jan Rubín, Malware Researcher
Ransomware
Every quarter, we summarize a total number of users that we’ve protected against ransomware (and other threats, too). Continuing from Q3/2022, the number of daily ransomware attacks detected has been slowly declining. During Q4, the total number dropped by 17%.
Have you ever wondered why the graph has the shape of a low-quality chainsaw? This effect comes down to ransomware’s weekly cycle – weekends are when activity is lowest. What’s more, fewer devices are used during weekends, so this also counts toward the Saturday and Sunday slowdowns.
Ransomware Overview
The list of countries with the highest risk ratio hasn’t significantly changed since Q3/2022. In most countries on the list, the number of attacks is declining. The only exception was Afghanistan, where the risk ratio is rising (this made Afghanistan an infamous victor of Q4/2022):
- Afghanistan (+45% quarter to quarter)
- Papua New Guinea (-18%)
- Mozambique (-13%)
- Ghana (-11%)
- Angola (+6%)
- Vietnam (-40%)
It’s worth noting that France also showed a 15% increase in risk ratio.
Ransomware Strains
STOP and WannaCry are the top two winners of the market share. Other ransomware strains show single-digit market share or lower:
- STOP (21%)
- WannaCry (20%)
- Thanatos (2%)
- HiddenTear (1%)
- Magniber (<1%)
- TargetCompany (<1%)
Stories
There’s no doubt that ransomware is a business. Ransomware gangs work as companies: They have their own managers, teams, websites, and blogs, and they even give interviews. But make no mistake – ransomware gangs are still very much illegal businesses. This was demonstrated by the court of Florida, who sentenced an affiliate of the Netwalker ransomware, Sebastien Vachon-Desjardins, to 20 years in prison for his attacks on an unspecified company in the state’s city of Tampa. Furthermore, $21.5 million were seized. We have no doubt that a 20-year sentence is a good warning to cybercriminals.
Although the Sodinokibi/REvil ransomware has been dead for almost a year, researchers from Palo Alto Networks suggested that it might have reincarnated as a different gang, called Ransom Cartel. This assumption is based on similarities between Ransom Cartel and Sodinokibi code. Also, some of Ransom Cartel’s file sharing links are the same as those previously used by the Sodinokibi gang. Because the source code of Sodinokibi never leaked, Ransom Cartel either tried to mimic Sodinokibi ransomware or they possessed the source code themselves.
LockBit ransomware keeps bringing news in Q4/2022. This gang stands behind many attacks: Asian Reinsurance Corporation, Porto de Lisboa (Port of Lisbon Administration), the UK’s Royal Mail, German multinational automotive group Continental , U.S. rail giant Wabtec Corporation, and the UK car dealer Pendragon. The ransom demand spans from tens of thousands of dollars (Asian Reinsurance Corporation) to $1.5 million (Porto de Lisboa) all the way to $60 million (in the case of Pendragon).
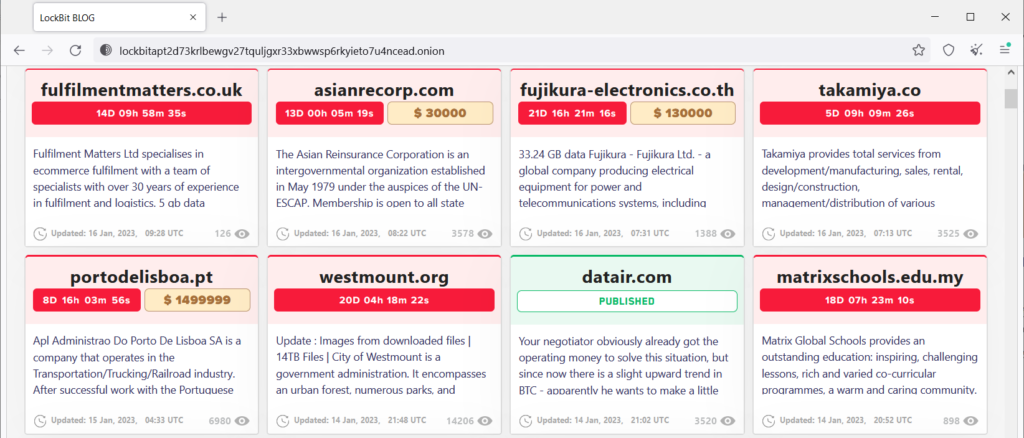
The LockBit gang commonly extort internal data of attacked companies and threaten to publish them if the ransom is not paid. And Lockbit follows through on this – for every attacked company, the gang has an entry on their blog and publish the data to anyone who is willing to pay the requested amount.
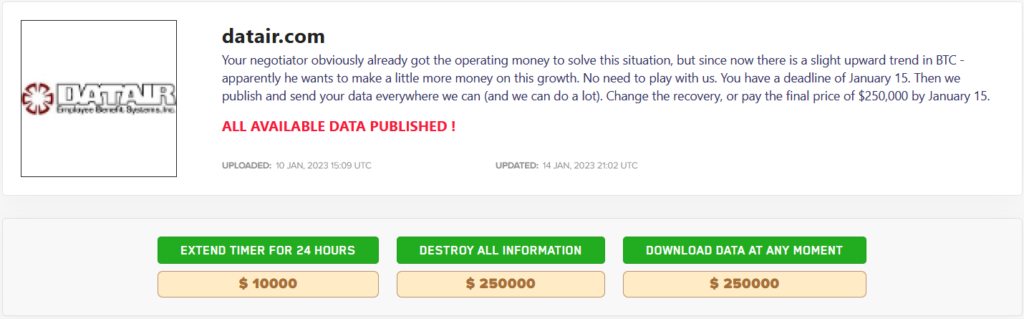
There was one attack that was different from the others. On December 18, 2022, the SickKids hospital was breached and their data encrypted. Two days later, however, the ransomware gang apologized for attacking the hospital. As part of their apology, they fired the gang member responsible for the attack and released a decryptor for free. The hospital later confirmed that they restored almost 50% of their encrypted data.
Although this might have come across as a thoughtful gesture during the Christmas season, we still hope that one day, LockBit members will stand at a court, just like the Netwalker affiliate did.
Apart from LockBit itself, there are also clones that emerged from the leaked LockBit builder. One of them was a pair of gangs called TommyLeaks and SchoolBoys. Those two gangs are actually one ransomware gang, as they use the same style of the negotiation site (the reasons for which remain unclear).
During Q4/2022, Avast helped victims of the MafiaWare666 ransomware by releasing a free decryptor for this strain.
Ladislav Zezula, Malware Researcher
Jakub Křoustek, Malware Research Director
Remote Access Trojans (RATs)
Compared to what we reported in Q3/2022, not much has changed in Q4/2022 in regards to remote access trojans (RATs). The most prevalent threats remain mostly the same as well as the list of countries with a high chance of RAT infection. The safest countries, according to our data, also changed only slightly.
In Q4/2022, France and the United States saw a large decrease in risk ratio, by 43% and 45% respectively, making them the safest countries in this quarter together with Switzerland and Japan. A similar level of decrease was observed in the Czech Republic (46%) and Austria (47%). New Zealand takes first place in this quarter with the risk ratio dropping by 56%.
On the other hand, the countries most in danger of RAT infection are Afghanistan, Iraq, and Yemen. The list is the same as in Q3/2022. The biggest increase in risk ratio happened in Algeria (22%), Iraq (13%), and China (11%). HWorm followed by njRAT are the most prevalent threats in Algeria and Iraq, while in China, it is Gh0stCringe and Havex.
The most prevalent RATs in our user base in Q4/2022 were:
- HWorm
- Warzone
- njRAT
- Remcos
- NanoCore
- AsyncRat
- NetWire
- QuasarRAT
- LimeRAT
- DarkComet
The list of top strains that we saw in Q4/2022 is nearly identical to what we reported in the previous quarter. njRAT dropped by one place on the list since it lost a considerable amount of its market share. We are unsure what caused the drop overall, but we have seen a campaign targeting Italy, France, and the USA. Similarly to Q3/2022, we saw a Warzone campaign in Hungary and a NetWire campaign targeting South Africa. Furthermore, Brazil and Argentina were hit by a campaign distributing QuasarRAT.
Other RATs with a significant increase in prevalence in Q4/2022 include:
- LimeRAT (299% increase)
- Gh0stCringe (122%)
- Nymeria (90%)
Based on our research, LimeRAT is still on the rise. Just as in Q3/2022, its prevalence was going up during Q4/2022. LimeRAT is mostly active in South and Southeast Asia as well as Latin America. Second on the list is Gh0stCringe, which was active almost exclusively in China with some infections in Taiwan and Hong Kong. Another strain with a big increase is Nymeria (also known as Loda). We see Nymeria spreading mainly in Turkey, Italy, and Mexico.
Our researchers discovered a new Nukesped RAT malware sample of The Lazarus group (APT38) for Linux operating systems and determined that the threat actor compiled the malware in a Red Hat 4.8.5-39 machine. This means that Nukesped RAT was not only written in Objective-C for MacOS (as found by previous investigations when analyzing similar samples) but also for infecting Linux machines.
Researchers from Zimperium zLabs discovered a new malicious browser extension called Cloud9, which acts like a RAT. This extension is quite capable and includes features ranging from stealing information like cookies, monitoring clipboard for passwords and credit card information, logging keystrokes, sending web requests, injecting ads, mining cryptocurrency to executing JavaScript code, and even exploiting browsers to take control of the entire device. The extension has exploits ready for Firefox, Internet Explorer, and Microsoft Edge. Although Cloud9 was not found in any of the official browser extension stores, it does spread via fraudulent Adobe Flash Player updates and by side-loading through malicious executables.
During Q4/2022, there may have been a shift in campaigns targeting Linux machines to mine cryptocurrency. The chain of events remains mostly the same (removing competition, deploying own mining malware, and setting persistence), but Trend Micro noticed a campaign which includes an unusual extra step in deploying a RAT. CHAOS RAT is a publicly available remote administration tool written in Go. The set of features allows for complete control of the infected device, as is common with RATs. CHAOS RAT itself isn’t new – it has been around for several years. However the shift from only mining cryptocurrencies to also possibly taking control of the whole device is both intriguing and concerning.
The Cyble Research and Intelligence Labs team spotted a new feature added to Venom RAT. According to them, the latest version of Venom RAT contains a stealer module which allows stealing information from various browsers. This means that it can now steal users’ cookies, passwords, and various other pieces of information that can be found in a browser. The malware is specifically interested in websites related to cryptocurrencies, banks, and adult content. Venom RAT can also steal credit card information. It can identify the most common types of credit cards by regular expressions.
RomCom is another threat actor which uses spoofed versions of popular software to distribute the RomCom RAT as reported by BlackBerry (and in a follow-up post). There are multiple known tools abused this way: Advanced IP Scanner, PDF Filler, SolarWinds Network Performance Monitor, KeePass, and PDF Reader Pro. The threat actor creates a fake website that offers a download of a trojanized version of the original tool. The website, including the domain where it’s hosted, looks nearly identical to the genuine one. The download bundle usually contains a RomCom RAT dropper and the original installer. According to BlackBerry’s research, features of the RomCom RAT include (but aren’t limited to) gathering information about local systems including taking screenshots and exfiltrating this data.
Ondřej Mokoš, Malware Researcher
David Álvarez, Malware Analyst
Rootkits
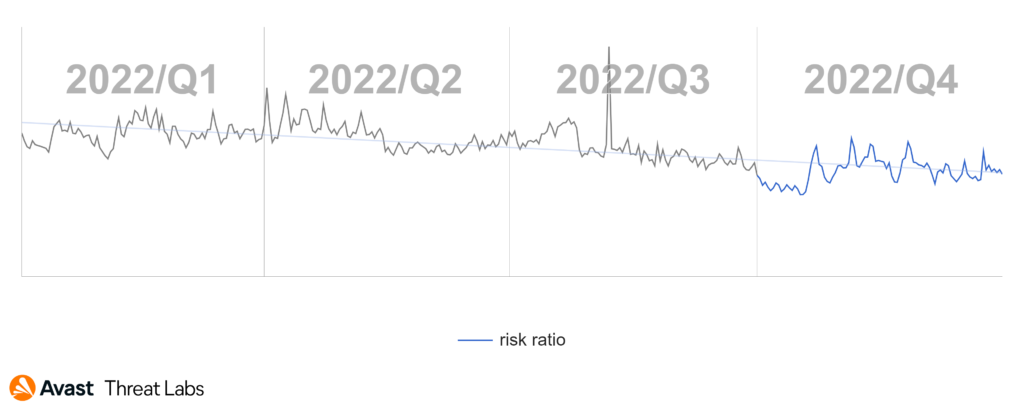
Rootkit activity continued to decline in Q4/2022. It’s evident that the rootkit activity during all of 2022 took a downward trend, as is shown in the chart below.
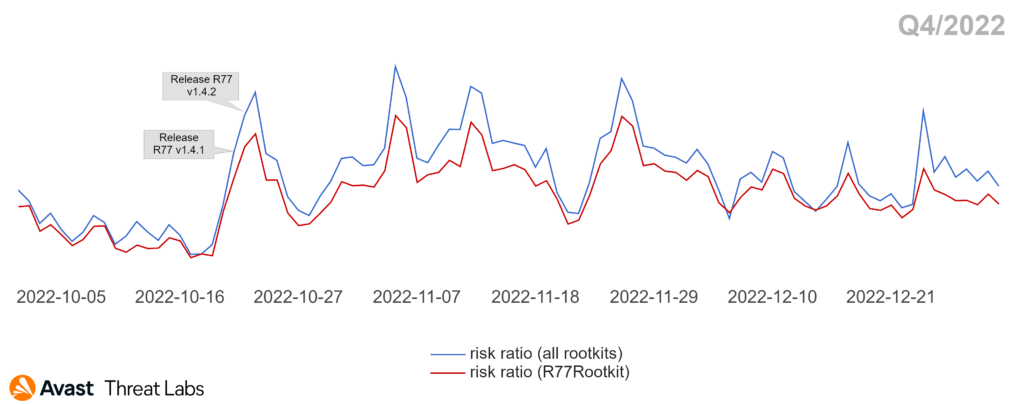
The distribution trend of rootkit strains confirmed our expectation that the primary strain in Q4/2022 (as well as the entire year) was the R77RK rootkit developed by the bytecode77 group. The market share of R77RK increased by about 43% compared to Q3/2022. Thus, R77RK held 56% of the total market share in Q4/2022. The chart below confirms the majority of the R77RK rootkit in Q4/2022.
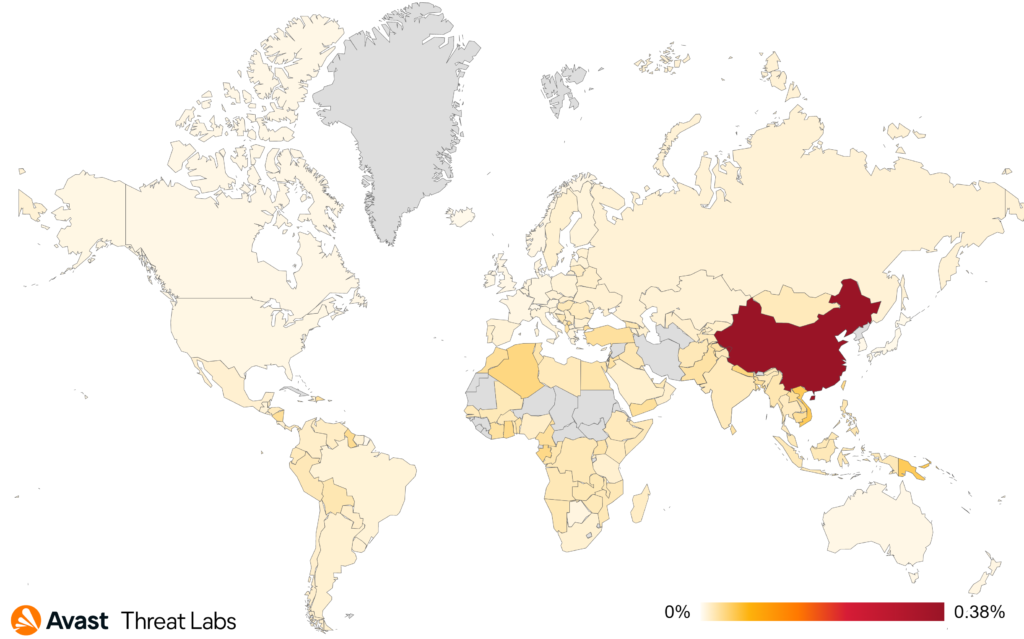
The map below displays R77RK’s activities in Q3/2022 and Q4/2022. In short, the R77RK’s activities moved from Northern Asia to North America. More specifically, we observed a significant increase in protected users in Colombia, Malaysia, Spain, Italy, and Mexico. On the other hand, the decrease of protected users is considerable in Ukraine and Turkey.
In detail, Avast Threat Labs monitors R77Rootkit as the dominant rootkit strain in 2022, including its open-source repository. In Q4/2022, two new R77RK releases affected the prevalence of this strain at the beginning of the quarter, as is illustrated in the chart above. The first of the releases reduced the size of the rootkit by 50% and fixed an important bug in the NtDeviceIoControlFile hook. Furthermore, the second release implemented code for the Windows Defender AMSI bypasses. These changes boosted the prestige of the rootkit, and the new features made the rootkit the most widespread and well-documented tool that can be easily abused for malicious activities. Fortunately, the open-source tools are highly detectable.
In Q4/2022, the global risk ratio of all rootkits is the same as in Q3/2022, and China remains the country where users have the highest risk of encountering a rootkit. This past quarter confirmed that R77RK is still 2022’s most popular open-source rootkit in the wild.
The remaining four identified strains of rootkits represent about 13% of the market share; however, these strains are on the decline. For completeness, the rootkit strains and their market shares are listed as follows:
- Alureon (4.71%)
- Perkesh (4.29%)
- Vrbone (2.03%)
- ZeroAccess (1.63%)
Martin Chlumecký, Malware Researcher
Vulnerabilities and Exploits
We discovered two sophisticated, zero-day exploits in the wild in Q4/2022. The first, CVE-2022-3723, was a type confusion in V8 and was used to carry out a remote code execution (RCE) attack against Google Chrome. On October 25, we reported this vulnerability to Google, who quickly rolled out a patch in just two days. The second zero-day was CVE-2023-21674, an LPE vulnerability in ALPC that allowed attackers to get from the browser sandbox all the way into the Windows kernel. Microsoft patched this one in the January Patch Tuesday update.
While these two vulnerabilities could have been chained together for a full RCE chain against Chromium-based browsers on Windows, we actually discovered them in two completely separate APT attacks. The CVE-2022-3723 exploit was chained with an n-day sandbox escape exploit for CVE-2020-0938. This attack was designed to target 32-bit Windows 7 and it would not work against later Windows versions because of mitigations such as win32k lockdown. CVE-2023-21674 was chained with an exploit for an unknown vulnerability. This was most likely a zero-day Chrome renderer RCE, which we unfortunately did not manage to recover because the exploit code was well protected by the attackers. We are still hunting for this and other exploits, and we hope we will be able to find it in the future so that we can better protect our users even against extremely well-resourced attackers.
When Blockchain is Not Truly Decentralized
One of the perks of cryptocurrencies is the fact that the blockchain they’re built on top of is decentralized and therefore can’t be stopped. Or can it?
In early October, Binance announced that two million BNB coins were stolen thanks to a bug in a cross-chain bridge that allows transfers between different blockchains (BEP2 and BSC in this case) being exploited. The vulnerability allowed attackers to mint new coins; therefore, no user funds were lost.
The fact that the attackers were able to create approximately $568 million in BNB coins for free isn’t the reason we mention this hack. What’s more significant is the fact that Binance was able to protect 80% of the coins by reaching out to all validators and requesting to stop the validation, effectively stopping the whole blockchain. This was quite an unprecedented move that demonstrated that blockchain technology on its own is not as resilient and secure as was declared and strongly depends on the distribution of validators/miners.
Insekt/Alchimist
In October 2022, Talos discovered a new attack framework called Alchimist along with a new malware called Insekt with remote administration capabilities. This is a cross-platform attack framework written in Go. On MacOS systems, it can use the implementation of the privilege escalation vulnerability (CVE-2021-4034) and the malware can provide a backdoor into the victim’s system.
Jan Vojtěšek, Malware Reseracher
Michal Salát, Threat Intelligence Director
Web Threats
In recent months, the cyber threat landscape has expanded significantly. Technologies such as smart devices and high-speed mobile networks have allowed for an always-connected vector of malware, fraud, and other complications. Every day, users rely on the internet more and more, and with that, they have to deal with a variety of potential threats that can lead to compromised accounts, lost money, or deleted personal data. From simple scam emails to bothersome push notifications, we’ve seen increased activity in these areas.
Refund and Invoice Scams
Another type of web threat that our users have often encountered are refund and invoice scams. Refund fraud covers a broad range of possible scenarios, including fraudulent emails alerting users that they have been charged twice for the service or product. These emails also contain links for users to request a refund, or alternatively, a phone number is provided for users to call fake support.
Businesses are popular targets for invoice fraud. In these scams, criminals send bills for goods or services that the business never ordered or received. The scam succeeds mainly because the invoices look legitimate and unsuspecting employees don’t look closely to see it’s not real. They simply make the payment thinking that someone else in their company placed the order.
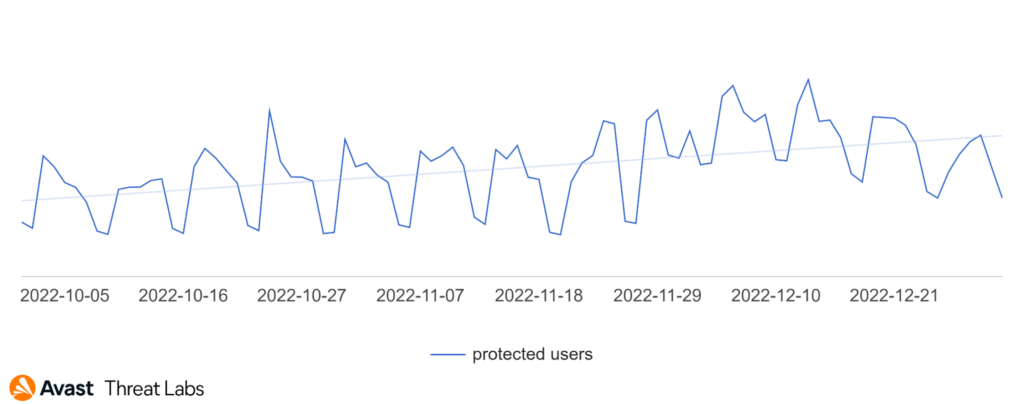
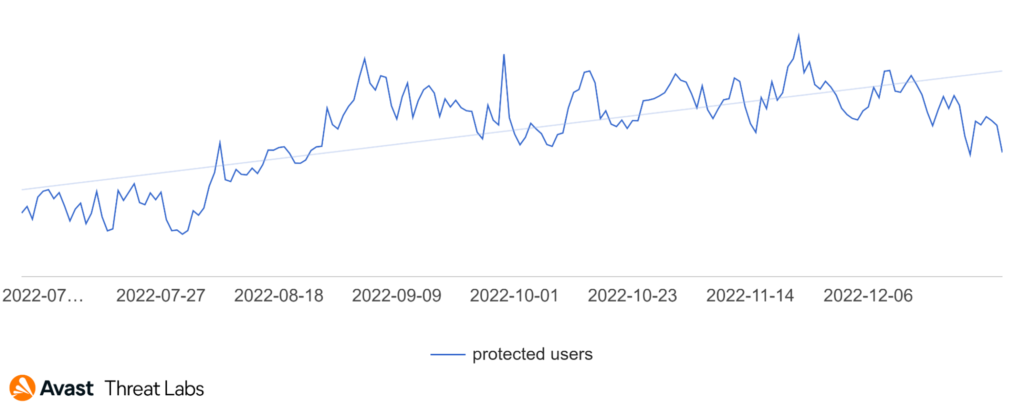
Looking at the graph above, it’s clear that the overall trend of refund and invoice scams during the quarter was positive. November was 14% more active overall compared to October and in December, Avast protected 22% more users against these threats.
In general, our data shows that the invoice scam technique spread via spam emails is far from obsolete. In fact, the opposite is true. When a victim is on the phone, the attacker can use his social engineering skills to elicit the user’s trust, similar to the technique used in technical support scams (TSS).
Technical support scams
Since September 2022, when we saw increased activity of TSS, this trend continued until the end of December, when activity began to decline slightly. In comparison with the entire year, the activity of technical support scams during the last two months of the year was very high.
The top affected countries remained the same as in Q3/2022. These countries include the United States, Brazil, Japan, Canada, and France.
Web-based Adware
The presence of web-based adware was also strong in Q4/2022. Here are some of the notorious examples seen during the quarter.
Personal and Payment Information
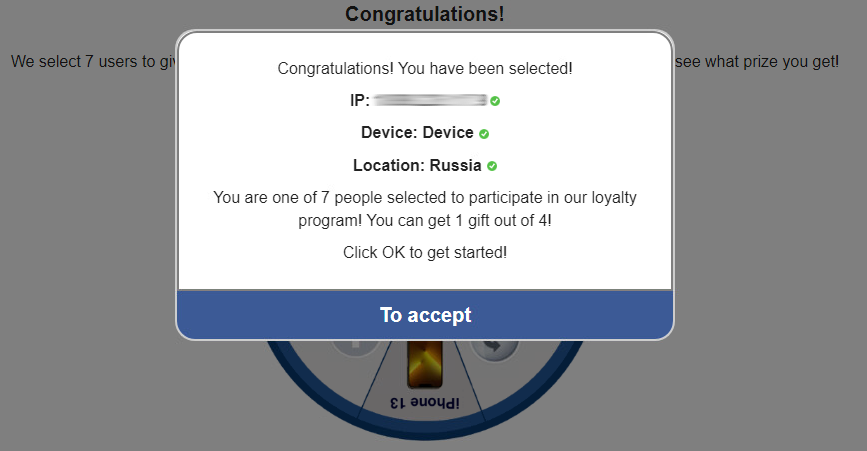
One example of how attackers effectively extort information from users is the promise of an easy win. The figure above shows one adware website. Here, the user spins roulette and wins, but it’s necessary for them to insert contact information and pay a symbolic handling fee using a credit card or Google/Apple Pay account. The website also includes a fake comments section to increase the credibility of this offer (see the figure below). Chat participants, including their names and photos, are entirely fictitious. Moreover, the discussion is often localized based on the geolocation of a victim’s IP.
Free Movies
Users also continue to search for free movies to watch online, and this is another excellent opportunity for adware action. In these attacks, the user is redirected to an adware website on which a “web player” starts to play the Universal Studios intro theme (see the example below).
The web player looks very realistic, but in reality, it’s a frame containing animation which creates the illusion that the movie has started playing – it even includes buffering in the progress bar. However, the movie gets frozen after a few seconds, which gives the impression that the film has stopped. At this point, the user is psychologically forced to click into the window, and they’ll be redirected to an unwanted or malicious page (see details above).
Security Warnings
This example is about spammers and attackers abusing the fear of fictitious security warnings to make users click and download a tool that “resolves” a security issue. It’s necessary to note that not all of the offered tools are dangerous, but they are located on the pages foisted by adware.
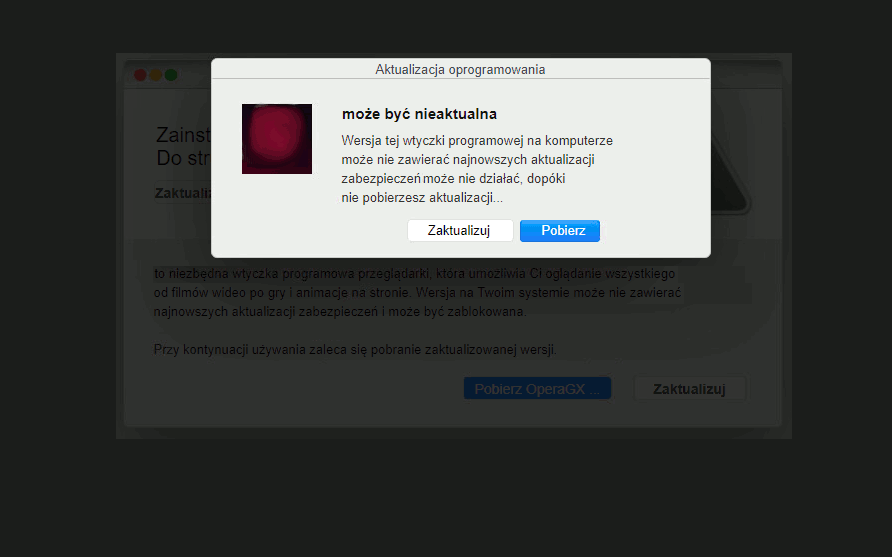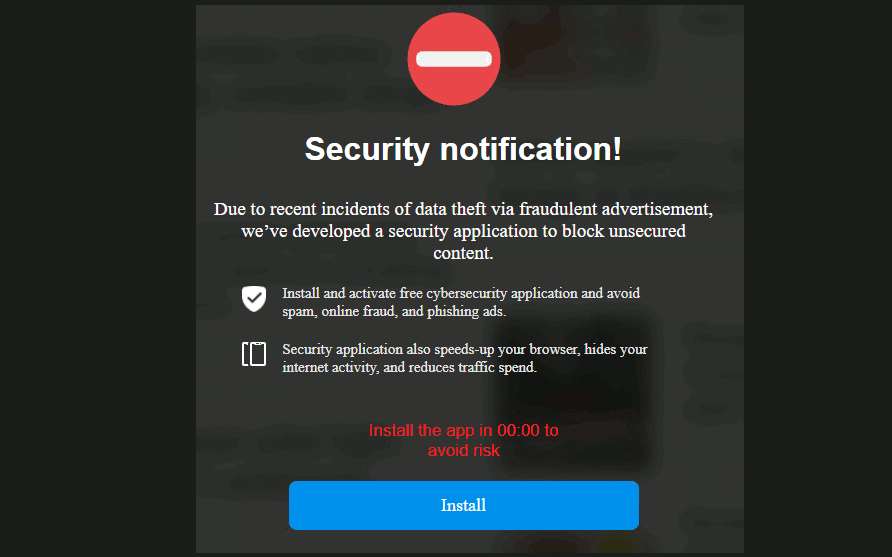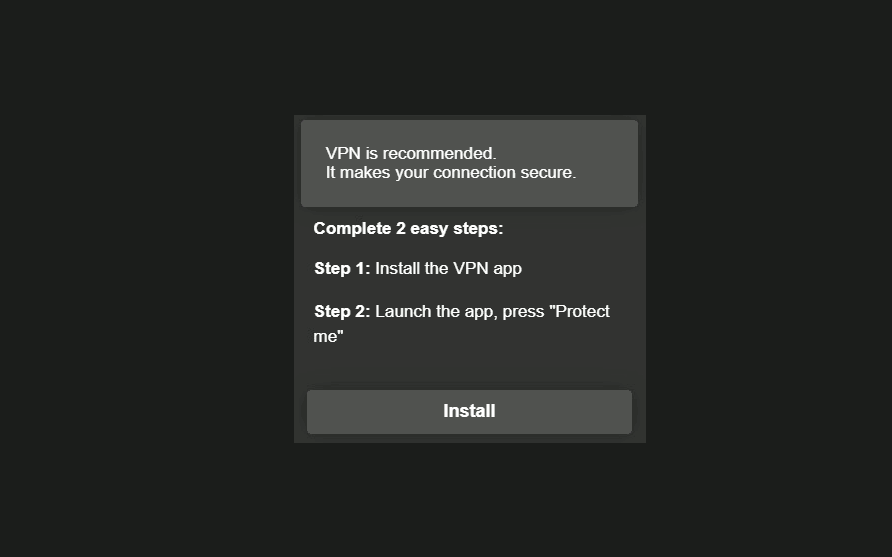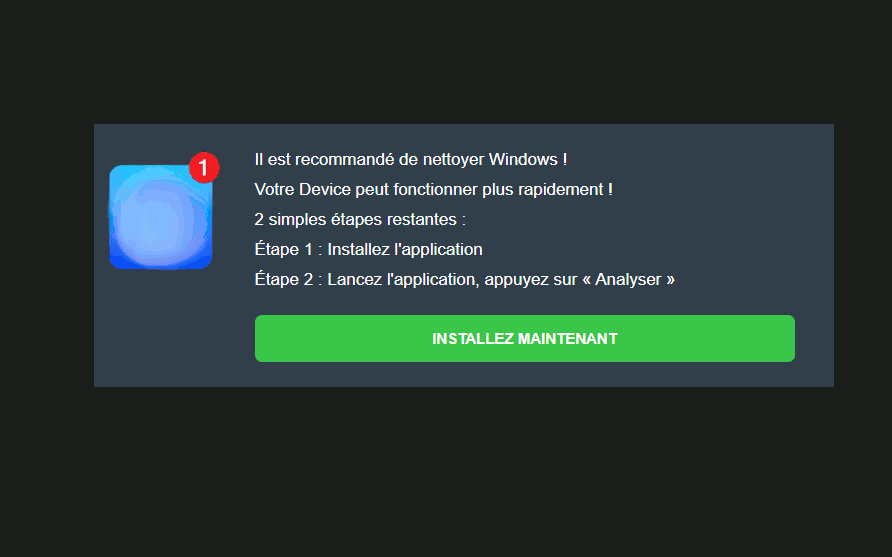
Alexej Savčin, Malware Analyst
Martin Chlumecký, Malware Researcher
Mobile-Related Threats
We have an interesting quarter behind us in the world of mobile threats, with several new discoveries of up-and-coming malware trying to pry a piece of the mobile pie. Whether it was a new Bully Facestealer grabbing victim logins through JavaScript browser injections or BrasDex, a banker that automates fraudulent payments and has links to a Windows banker, it’s evident that malware actors have been busy yet again. Alongside these discoveries are some insights on what established malware strains are up to, whether they are on the rise or decline and what their newest version brings.
We’ve picked the most prevalent families of malware on mobile devices according to our metrics and provide some hopefully useful and interesting insights based on those internal metrics coupled with pointers to the aforementioned new discoveries. Read on to find out more.
Adware
Q4/2022 was yet another quarter where adware continues to rule the mobile threat landscape, having the highest number of affected users. Using inventive ways to bring in advertising revenue, adware finds ways to sneak onto user devices and displays intrusive ads. The user is often unaware of the source of these ads, as adware uses several tricks to sneak onto the victim’s device and then proceeds to hide out of the victim’s sight.
HiddenAds rank at the top of the adware strains, utilizing victim’s devices to display out-of-context ads that often block the whole screen even when browsing or otherwise using the device. Of note is a new version of HiddenAds was discovered by Malwarebytes on the Play Store. It masquerades as a variety of Bluetooth utility apps, then proceeds to open up advertisements and even phishing sites in the background of Chrome browser. Victims open up their browser to be met with an unpleasant surprise.
Coming in at second place, FakeAdBlockers keep staying true to their name, bringing in extra unwanted adverts instead of blocking them. Upon installation, they tend to disappear from the home screen and start their malicious activity with a few hours delay. Contrary to HiddenAds, they keep spreading through unofficial channels, such as notification alerts from infected websites that attempt to coerce the victim into installing this adware. Both strains often imitate games, camera filters, and wallpaper apps, among others. Users are advised to avoid third-party stores and unknown websites for application downloads in order to avoid adware or even other malware.
A newcomer this quarter is LiveClick, discovered by McAfee. It comes disguised as a variety of utility apps such as notes or a flashlight app. Once installed, it delays its malicious activity until it senses that the device is not in use. Silently, in the background, it starts opening up specific websites and imitating user behavior to simulate clicks on adverts, bringing in advertising revenue to the malicious actors. While not directly affecting the user experience, this adware will lead to increased power use of the device as well as higher network traffic, which may be an issue for victims with a limited data plan. It also undermines the mobile advertising ecosystem with fake clicks.
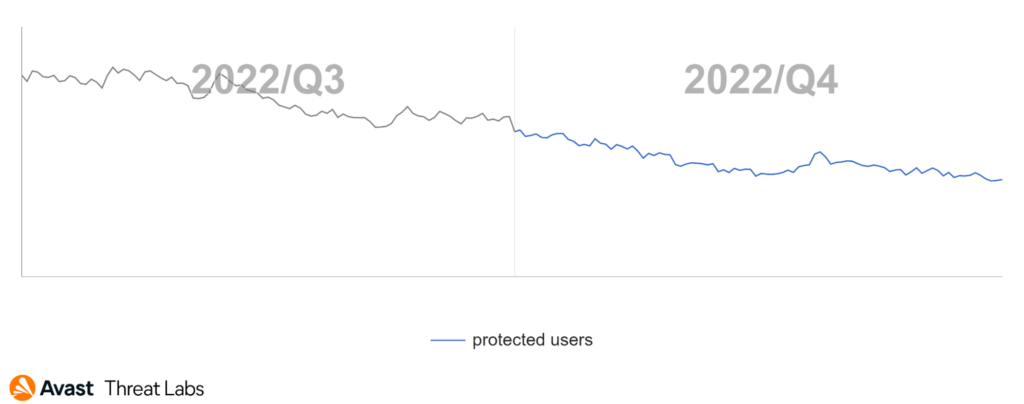
We have observed a mild decline in the number of affected users since last quarter. While adware continues to dominate the mobile threat landscape, this likely points to a weakening of adware infrastructure and increased difficulty in accessing the Play Store with new strains of HiddenAds. It remains to be seen if this trend will continue into 2023.
Users in both Americas, Asia, and newly, Europe, are most likely to face adware threats. Brazil and India maintain their top spots in the adware category, while the United States has gone down to sixth place. Of note is that Italy and Spain have also reached the top 10 most affected countries by adware. With Italy being the only outlier (a 16% increase), we see a drop in affected users for most countries, with a more than 30% drop in India, Brazil, and Mexico. Despite this, adware is still the most common threat that mobile phone users must contend with today.
Bankers
The banker sphere sees little change compared to last quarter. Cerberus/Alien keeps its top spot by protected users, followed by Hydra, RoamingMantis, and Flubot. Only Hydra maintained its numbers this quarter, while the rest lost over 25% on average (with Flubot ceding over 35% of its victim base, according to our metrics). The continued positive effect of the Flubot group disbanding by Europol can be clearly seen here; judging by the decreasing numbers, it is likely the general banker infrastructure has been affected as well.
Continued reliance on SMS phishing seems to have less effect, as the banker sphere is on a long-term downward trend in terms of affected users. While delivery methods haven’t really changed, some new techniques were used by BrasDex, a new banker targeting Brazil discovered by ThreatFabric that appears to share C2 dashboards with Windows banking malware, Casbaneiro. Using accessibility features of victim’s devices to take them over and monitor all inputs, the banker is able to automate fraudulent payments that can be sent in seconds through a popular payment platform. This potentially allows for a large scale of money extraction from the victim’s accounts. We’ll have to wait and see if Brazil will face more of these targeted bankers.
Of note is the discovery of Vultur and Sharkbot bankers being delivered via droppers on the Play Store, gathering hundreds of thousands of downloads before being removed. Both bankers employed fairly novel methods of payload delivery or detection avoidance. In the case of Vultur, the Brunhilda dropper used steganography (hiding secret data within an ordinary file) to avoid detection. Some time after installation, it delivered its payload under the guise of an app update, allowing extensive access to the victim’s device. The dropper that delivered Sharkbot bankers would only send the payload to a limited number of victims in specific countries – and only if they had target bank apps installed. While limiting its reach, it’s less likely to be discovered this way, allowing it to stay on the Play Store longer.
According to our findings, there is an evident long-term downward trend in the banking sphere. We observed a drop of 20% in affected users in Q4/2022 compared to Q3/2022. We attribute this to Flubot’s demise as well as decreased effectiveness of established methods of banker payload delivery.
Top affected countries stay the same this quarter: Spain, Turkey, and France have the most affected users by banker malware on mobile devices. On average, we’ve seen a 25% decrease in affected users in top countries. Of note is Brazil, where we saw an 84% increase in affected users, likely due to the new BrasDex banker.
TrojanSMS
Mirroring last quarter, UltimaSMS and GriftHorse have fully disappeared from the mobile sphere, while SMSFactory and Darkherring remain the top strains of the TrojanSMS family in Q4/2022. We’ve also seen some more generic and less sophisticated applications affecting increased numbers of users.
TrojanSMS generally relies on premium SMS subscriptions or sending SMS messages to premium numbers to rob victim’s of their money. Coupled with stealth features such as hiding their icon, deleting a sent SMS, or even simulating functionality, this malware can remain undetected or forgotten on victim’s devices and continue siphoning money to their creators.
As mentioned last quarter, due to its method of spread, SMSFactory continues to be prevalent and keeps spreading to new devices. It has again gone through some minor adjustments and changes in delivery websites, but it remains the top TrojanSMS strain worldwide. Surprisingly, DarkHerring, which originally propagated on Play Store, appears to be resurging in numbers due some applications reappearing on third-party stores and fake app stores. We are possibly seeing some attempt at resurrecting the strain by adjusting its method of spread.
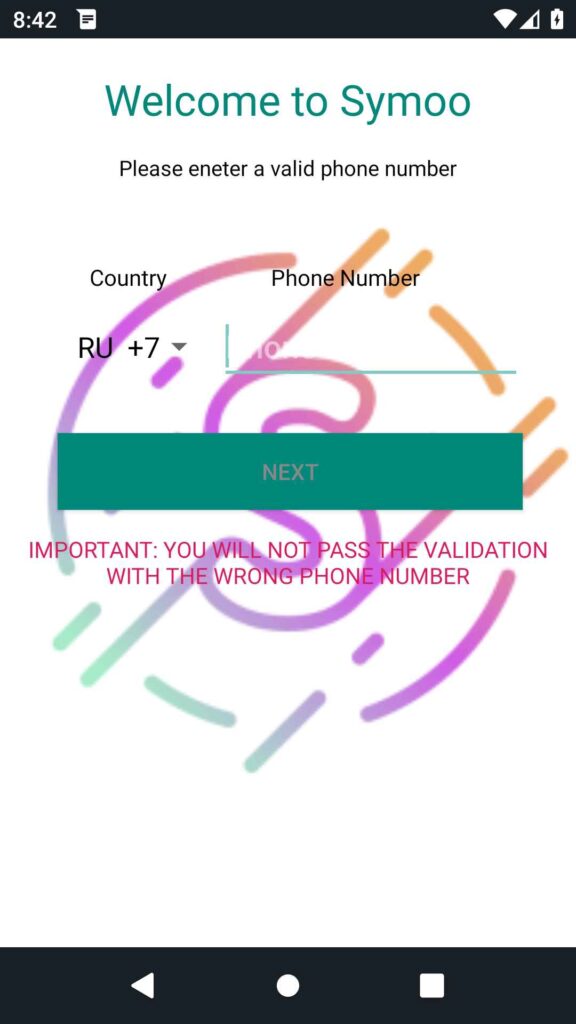
While this quarter has been reasonably quiet in terms of new discoveries, an interesting find by EvinaTech on the Play Store showcased a different type of TrojanSMS as compared to the previously mentioned strains. As a fake SMS messenger, in actuality it uses the victim’s device as an SMS relay for account creation on popular sites such as Google, Facebook, and Microsoft. It asks for the victim’s number, then shows a fake loading screen that leads nowhere. While the loading screen is up, the malware creates fake accounts for the aforementioned sites by using the device’s SMS functions. Users generally uninstall the application as it appears stuck on the loading screen, but its role is already fulfilled. It remains to be seen if this type of account creating malware will reappear in the future.
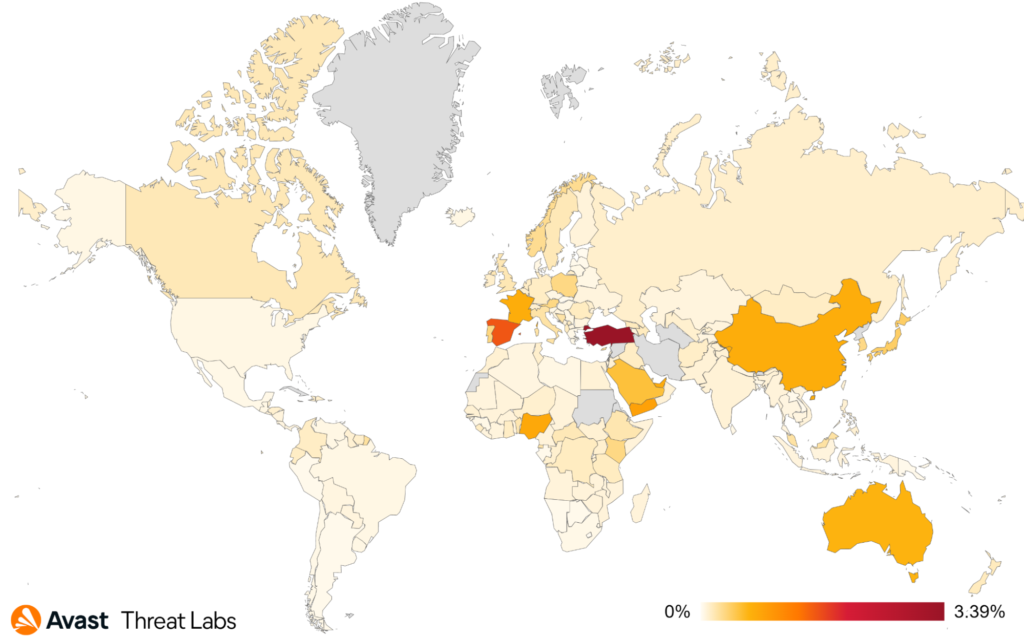
Brazil maintains its top spot in terms of protected users, followed by Russia, Egypt, the United States, and Ukraine. Only Egypt has seen a 12% increase, while the other top countries see a varied decrease in affected users. Iraq and Azerbaijan have the highest risk ratios, as can be seen in the map below.
We’ve observed a 32% decrease in protected users in Q4/2022, likely due to the lack of new entries into the TrojanSMS family coupled with the exit of UltimaSMS and Grifthorse that were widespread late last year and early this year.
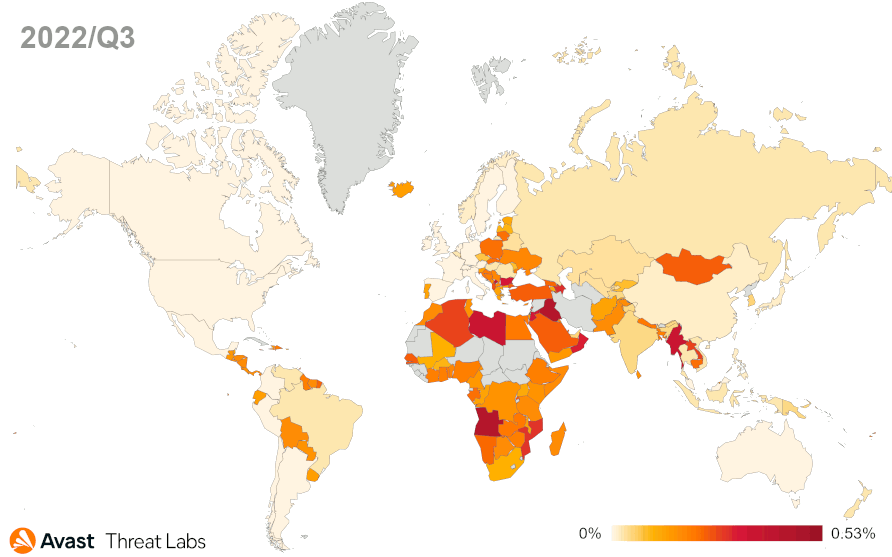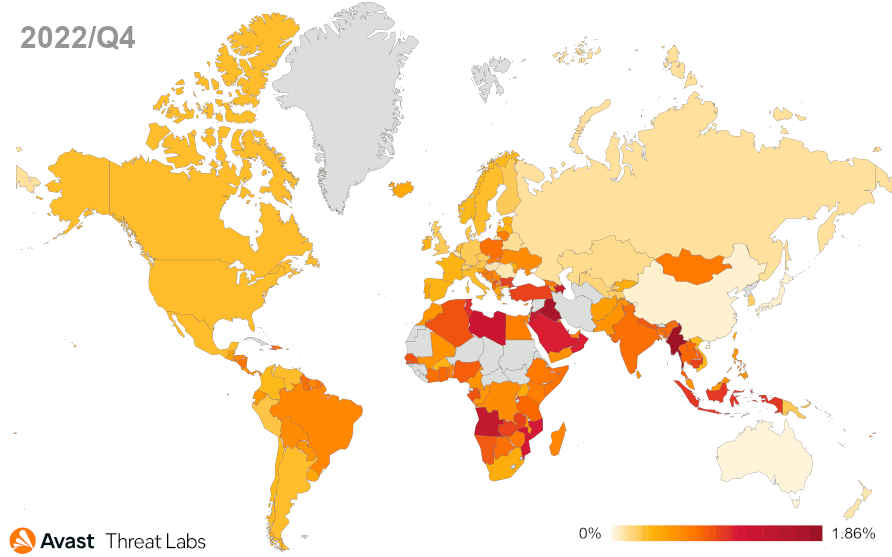
Spyware
A persistent threat to users worldwide, Spyware continued its spread in Q4/2022 with a continuation of previously discovered variants such as Spymax, malicious WhatsApp mods, and FaceStealer.
As evident from its name, Spyware spies on its victims, invading their digital privacy with the intent to misuse their details, activity, photos, messages, location, and other personal information. Login credentials, banking details, and crypto wallet addresses are often part of the steal as of late. Spymax has slowly been evolving to acquire most of these over the years and continues to do so this quarter. Often coming in heavily obfuscated, it imitates the names and icons of popular applications but is indeed a malware attempting to hide its true purpose. SMS and malicious redirects feed this malware to unsuspecting victims, and it remains the most prevalent spyware this quarter.
FaceStealer, a more recent addition from last year, has continued its spread, albeit with a lower number of affected users. Its intent is mainly to steal login credentials to popular social media, with more recent strains expanding this intent to other platforms as well. With a variety of FaceStealer applications discovered early this quarter by Meta, we are continuously observing smaller intrusions of this malware on the Play Store. While smaller in impact on their own, even a few users falling victim to this malware can cause a great amount of personal harm. Towards the end of the quarter, Zimperium reported on a larger wave of FaceStealer, dubbed Bully, on the Play Store. Disguised as book reading applications, this strain was primarily targeting Vietnamese users. Using JavaScript injection into the WebView browser, it was able to hijack the legitimate Facebook login screen and steal user credentials. Various obfuscation methods are used to disguise the strings before they are sent to their C2 server.
Spyware WhatsApp mods have also contributed to the damage done this quarter, with new malicious modifications being discovered by Kaspersky. Imitating a popular modification, the actors behind the malware were able to sneak adverts for their trojanized mod onto popular ad platforms. Once installed, it would act as the original modification but install other malware with it. Alongside this, it would steal private keys related to the WhatsApp account, which could be used to steal the account itself. As per last quarter, we advise users to avoid downloading modifications for WhatsApp or other messengers, as they generally do not come from an official app store. This means that there are no security checks in place and users don’t know what the modification could contain. Whatsapp’s FAQ warns that it could also lead to a suspension or an account ban.
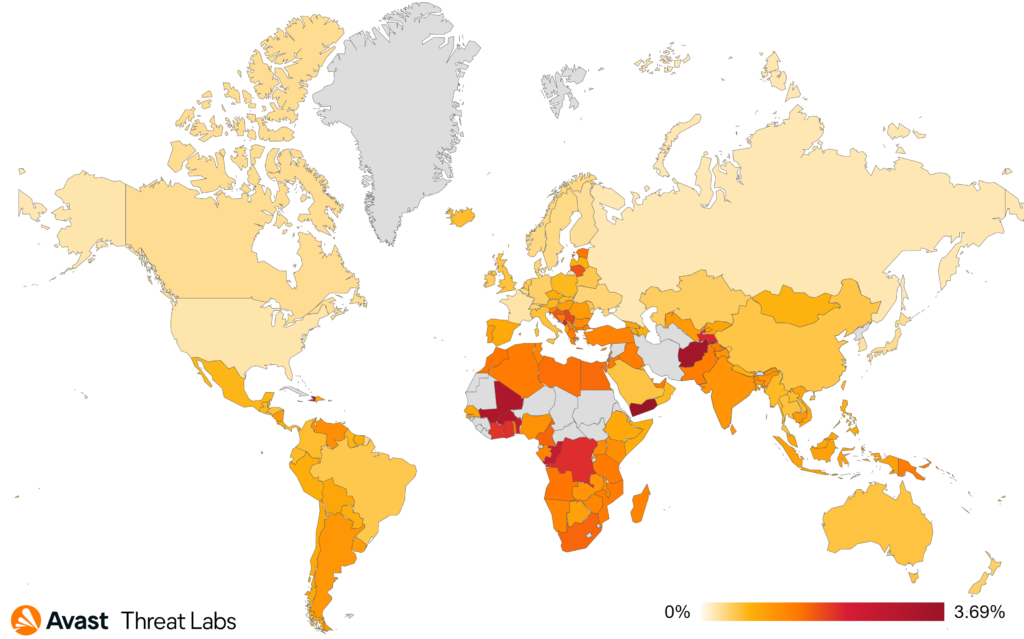
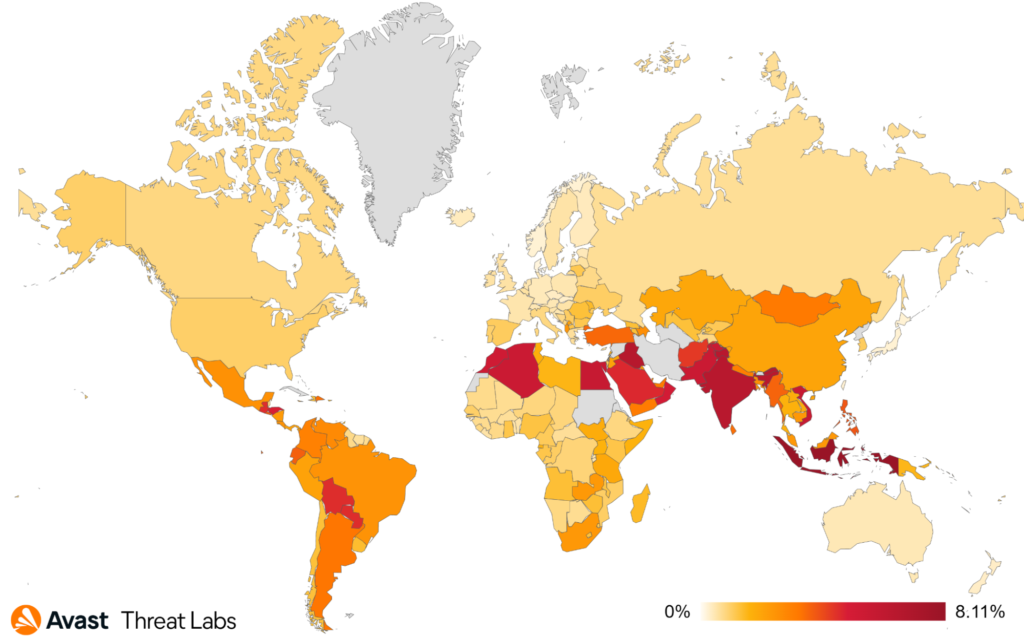
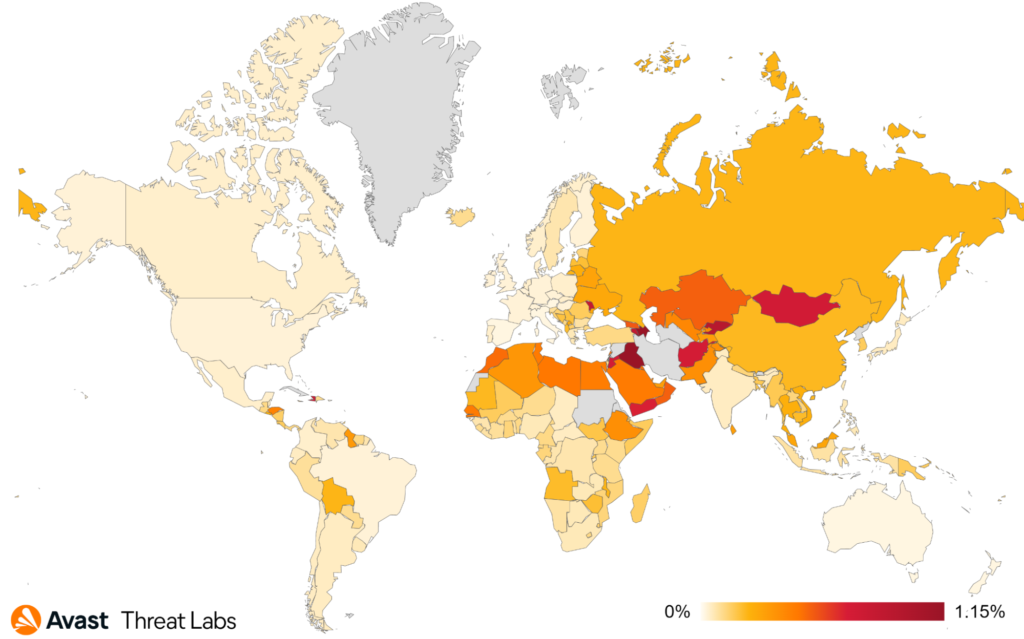
We record the most protected users in Brazil, India, Egypt, the United States, and Turkey in Q4/2022. The top five affected countries remain unchanged from last quarter. Brazil and Turkey both see an increase in affected users, while Egypt and India see a reasonably sharp decline. Users in Yemen are most at risk of encountering spyware, as can be seen in the map below.
A slight downward trend in overall protected users still doesn’t diminish the danger posed by these malicious applications. It is likely that we will see an uptick in affected users into the future, as we’ve observed a fair few new additions to the spyware family.
Jakub Vávra, Malware Analyst
Acknowledgements / Credits
Malware researchers
Adolf Středa
Alexej Savčin
David Álvarez
Igor Morgenstern
Jakub Křoustek
Jakub Vávra
Jan Rubín
Jan Vojtěšek
Ladislav Zezula
Luigino Camastra
Martin Chlumecký
Michal Salát
Ondřej Mokoš
Vladimír Žalud
Data analysts
Pavol Plaskoň
Communications
Grace Macej
Marina Ziegler